Imagine handing your house key to a stranger you
just met—all so they could deliver a package faster. Would you do it?
That key is your bank username and password. The stranger is a data aggregator like Plaid. And the package? The convenience of modern finance—Venmo transfers, budgeting apps, and instant credit approvals.
If you’ve used any financial app in the last five years, you have
already done this. You wanted efficiency, saw Plaid’s familiar login screen,
typed your credentials, and moved on.
But here’s the question few ask: Did you realize that until very
recently, this simple act meant exposing nearly everything in your bank
account—and that the law protecting you is now frozen?
Welcome to the hidden crossroads of US Open Banking. We were promised transparency and choice, yet the very system that powers convenience still carries deep security uncertainty. Let’s unpack what went wrong, what’s changing, and how you can safeguard your financial data today.
When
we talk about Plaid data privacy and security, the company emphasizes that it
doesn’t sell user data. That’s true. The real risk came from the original
connection method itself.
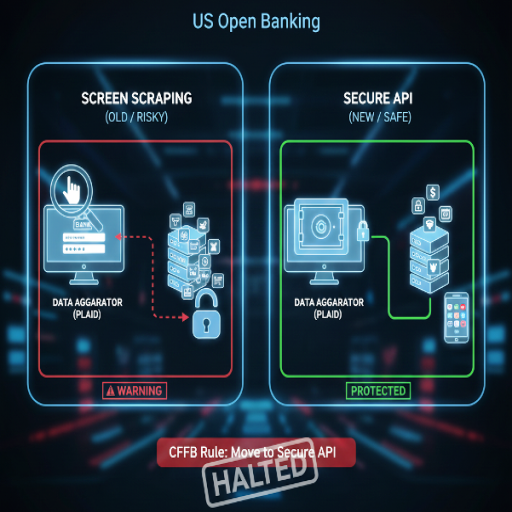
Screen scraping allowed an
aggregator to log in to your bank using your actual username and password, then
copy the visible data. It was the digital equivalent of giving a stranger your
master key so they could photograph your filing cabinet.
This
exposed two major issues:
1. Credential Exposure — Even
if Plaid replaced your credentials with a secure token, the initial handoff
bypassed your bank’s protective layers.
2. Data Over-Collection — Because the entire online banking view was scraped, aggregators often collected far more data than needed.
In
2022, this practice led to a $58 million class-action settlement against Plaid
for alleged lack of transparency. The company responded with new disclosure
tools and invested heavily in replacing scraping with secure APIs—direct,
permission-based data pipelines issued by banks themselves.
By
early 2024, Plaid reported that 75 percent of its data traffic had already transitioned
to or committed to API-based connections. This is the model the future depends
on—but legal uncertainty now threatens to delay that transition.
Recognizing the dangers of uncontrolled data sharing, the Consumer Financial Protection Bureau (CFPB) finalized the Personal Financial Data Rights Rule (under Section 1033 of the Dodd-Frank Act) in October 2024.
It aimed to ban fees for data access, enforce clear consent, and phase out
screen scraping altogether.
However,
in October 2025, a U.S. District Court issued a stay, freezing enforcement
after banking associations filed lawsuits challenging the rule. The CFPB then
announced a full reconsideration process.
Here’s
what that means for you right now:
No-Fee Guarantee at Risk: The
agency is reconsidering whether banks can charge for data access. If allowed,
even viewing your own financial data through an app might come with a cost.
Restricted Third-Party Access: Regulators
are debating whether only fiduciary entities may handle consumer data, which
could reduce the range of financial tools available.
Missing Liability Framework: It remains unclear who is responsible when unauthorized transactions or data breaches occur—banks, apps, or aggregators.
This
pause means the long-awaited security reforms under US Open Banking consumer
protection rules are delayed, extending the lifespan of riskier data-sharing
systems.
For a
deeper look at the legal structure, read The
CFPB’s Section 1033 Rule: How the New Regulation Will Redefine Data Ownership.
The
October 2025 freeze makes one reality clear—your data protection starts with
you. Until the new rule resumes, these actions will keep your information safer:
1. Audit Your
Connections via the Plaid Portal: Visit my.plaid.com to review all
connected apps. Remove any that you no longer use. Every revocation limits
exposure.
2. Favor Secure API
Connections: When
adding new services, check if they use your bank’s branded login (OAuth or
“Sign in with [Bank Name]”). That means your credentials stay with the bank—not
the aggregator.
3. Enable Multi-Factor
Authentication (MFA): Always
require a second verification method for any account that links to your
financial data.
4. Demand Transparency: Before
granting access, read the app’s privacy policy. Look for clear limits on data
use, sharing, and deletion.
5. Support a Strong
Liability Framework: Add
your voice during CFPB public-comment periods. Advocate for rules that make
institutions accountable for security lapses.
Explore
the technical transformation in From
Screen Scraping to Secure APIs: The Evolution of FinTech Data Sharing and Why
It Matters to You.
The Plaid Lie: The Myth of Effortless Safety
The
phrase “Plaid Lie” has become shorthand for an uncomfortable truth: users
assumed the familiar Plaid login meant total safety. It never did.
Even
as the company has strengthened its systems, the overall open-banking network
remains fragmented. Some banks still rely on legacy methods; some apps still
use indirect connections.
The
result is a patchwork of responsibility where consumers often face uncertainty
about who actually safeguards their money.
Until
consistent federal standards return, informed caution is the only defense.
Looking
ahead, several outcomes are likely:
Revised Rulemaking (2026): The
CFPB is expected to release an updated version clarifying fee policies and
liability standards.
Industry Push for Standard APIs: Banks
and fintechs continue to align on Financial-grade API (FAPI) protocols for
encrypted, token-based sharing.
Public Education Efforts: Expect greater emphasis on consumer awareness campaigns around data rights and revocation options.
If
properly implemented, US Open Banking could still deliver financial freedom—but
not until the foundations are rebuilt on security, not convenience.
Q1: What is the status of the CFPB’s
Personal Financial Data Rights Rule?
The rule finalized in 2024 is on hold. A federal court stayed
enforcement in October 2025, and the CFPB is reconsidering several provisions
before re-issuing guidance, expected sometime in 2026.
Q2: Why is
screen scraping considered unsafe?
It relies on sharing your real login
credentials with third parties, allowing broad data extraction beyond what an
app requires. A secure API
eliminates that exposure by using temporary access tokens generated by your
bank.
Q3: Has Plaid
improved its data-handling practices?
Yes. After a 2022 settlement, Plaid
implemented clearer disclosures, expanded its user control portal, and shifted most data traffic to secure APIs.
Still, consumers should manually revoke unused app access.
Q4: Why might
banks charge fees for data access?
Some financial institutions claim
maintaining open-data APIs adds cost. The CFPB is evaluating whether limited
fees are permissible—a proposal that consumer groups argue undermines open
banking’s purpose.
Q5: How can I
see which apps have my data?
Go to my.plaid.com
and sign in using your linked email. You’ll see all authorized apps and can
revoke access instantly.
Q6: What should
I do if a connected app is breached?
Immediately revoke its access in
Plaid or your bank portal, change your bank password, and notify your bank’s
fraud department. Keep documentation of all alerts.
Q7: Are secure
APIs already active in the U.S.?
Yes. Major institutions like
JPMorgan Chase, Wells Fargo, and Bank of America already use token-based
connections with Plaid and other aggregators. The challenge lies in full
adoption across smaller banks.
Q8: Does the
frozen rule affect my daily app use?
Not directly, but it delays uniform
security standards. You may still encounter apps using outdated scraping
technology. Favor apps listing “secure API” or “OAuth” connections.
Q9: Who is
responsible if unauthorized transactions occur through an app?
Currently, liability is shared and
case-specific. One goal of the revised CFPB rule is to establish a clear,
consistent liability chain.
Q10: How can
consumers influence the rule’s outcome?
Public comments shape revisions.
Submitting feedback on the CFPB’s website or supporting consumer advocacy
groups ensures that user-centric data protections stay a priority.
Comments (0)
Leave a Comment
No comments yet
Be the first to share your thoughts!